EU triangle: data protection, data economy and IT security
The implementation of the General Data Protection Regulation (GDPR) continues to pose a major challenge for many companies. In addition, they are now facing new EU regulations in the areas of the digital economy and cyber security.
How do we ensure that we don't lose track of all existing regulations and what role does data protection play in this?
According to a recent survey by German Chamber of Industry and Commerce (DIHK)which was conducted among 4,900 companies, around 80% of the companies surveyed still associate a "high to extreme" level of effort with the implementation of the GDPR. The tension between the GDPR and various EU regulations on the data economy, such as the Data Act, is particularly problematic.
About the author

EU triangle: data protection, data economy and IT security
The implementation of the General Data Protection Regulation (GDPR) continues to pose a major challenge for many companies. In addition, they are now facing new EU regulations in the areas of the digital economy and cyber security.
How do we ensure that we don't lose track of all existing regulations and what role does data protection play in this?
According to a recent survey by German Chamber of Industry and Commerce (DIHK)which was conducted among 4,900 companies, around 80% of the companies surveyed still associate a "high to extreme" level of effort with the implementation of the GDPR. The tension between the GDPR and various EU regulations on the data economy, such as the Data Act, is particularly problematic.
Tension between the Data Act and GDPR
The Data Actwhich came into force in January 2024 and will apply throughout the EU from 12 September 2025, creates a new legal framework for the exchange and use of data related to connected products or services. This applies to both personal and non-personal data. In the case of personal data, the Data Act supplements the right to data portability in accordance with Art. 20 GDPR.
The transfer of personal data by the data controller from one user (1) to another user (2) or to a third party data recipient poses a particular challenge.
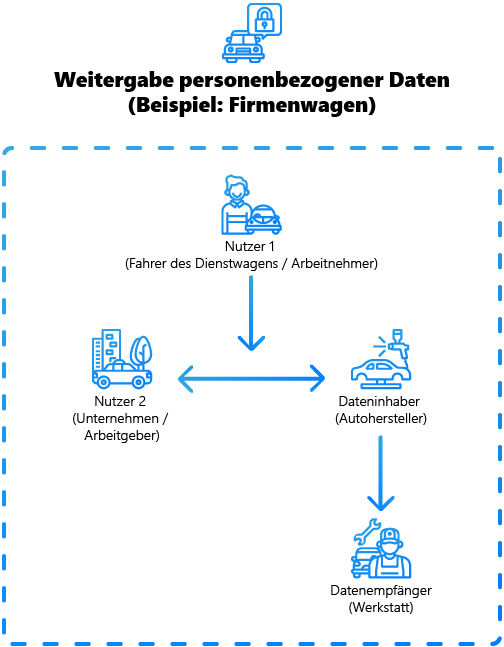
The implementation of data exchange between data owner, user and data recipient, derived from the Data Act, harbours the risk of a breach of the GDPR. At the same time, the refusal of the data access request could potentially violate the Data Act.
According to Article 1(3) of the Data Act, the applicability of previous Union legislation remains unaffected. It is therefore important to determine the legal basis for data processing in accordance with Article 6 (and, if applicable, Article 9) of the GDPR and to draft the contracts between the parties accordingly. Similar to the GDPR, the European Commission will draft non-binding model contractual clauses for data access and use and non-binding standard contractual clauses for cloud computing contracts (under Article 42 of the Data Act, the deadline for this is 12 September 2025) to assist parties in drafting and negotiating contracts with fair, reasonable and non-discriminatory contractual rights and obligations.
Data protection in the service of IT security
Despite the challenges of implementing the GDPR, more than half of companies emphasise the increased importance of data protection, particularly in light of the threat of cyberattacks.
The NIS-2 Directivewhich must be transposed into national law by 17 October 2024, aims to increase cybersecurity in the EU. To this end, companies categorised as operators of essential services in 18 sectors must take appropriate security measures and inform national authorities of serious incidents. Consequently, data protection also plays a special role here, as the protection of personal data may be jeopardised in the event of information security incidents.
The competent authorities for network and information systems, central contact points and CSIRTs (Computer Security Incident Response Teams) may process personal data for the necessary purposes of the NIS-2 Directive on the basis of an appropriate legal basis under the GDPR. The requirement to "provide for appropriate and specific measures to protect the fundamental rights and interests of natural persons, including technical restrictions on the further use of such data and the application of state-of-the-art security and data protection measures such as pseudonymisation or encryption [...]" (Recital 121 of the NIS-2 Directive) are compatible with the requirements of the GDPR.

Is your company also affected by the NIS2 Directive? Take our free NIS2 quick test and find out whether your company is affected by the NIS2 Directive:
There is no way around the GDPR
Even if the complexity increases due to the new EU regulations, one thing is clear: there is no way around the GDPR! More than 70% of the companies surveyed in the DIHK survey stated that they would like to see guidelines and recommendations that are practical, clear and precisely formulated. More than half also want specific sample forms and checklists. Our targeted support for GDPR compliance offers exactly that. Find out more at this link:
Determining the legal basis for data processing
(Art. 6, GDPR)Enable the right to data portability
(Art. 20, GDPR)
Implement appropriate technical and organisational measures (TOMs)
(Art. 32, GDPR)
Conclude corresponding contracts
(e.g. for the purpose of order processing or data transfer to third parties)
Do you have any questions?
If you have any questions about this or would like support with data protection requirements, please contact us.



